Important Things to Identify in IoT Security
- Technology Blog May 09,2018

IoT deployment is rapidly growing across the world. The significant concept of these developments is the security of the Internet of Things development. It has been recognized by the business that the security is needed at the very initial stage of deployment. It is becoming the hot concern of today’s market. Whether a secure development is needed or operations of scalable IoT applications to connect the virtual and real world, they security if major concern for all objects, people, and system. IoT security is crucial but complex. Therefore, in this article, we’ll address the essential object and insights for its identification.
IoT Security Investment
IoT adoption is rapidly increasing within the industries. End-users are spending to third-party solutions in order to attain the security. Along with third-party solutions, there are different tools available in the market that are provided by the IoT platform associated with security concerns. Security requirement is important for all established firms and the startups. Vendors are addressing the security challenges for industries across the world. The investment in IoT security is assumed to be increased significantly in coming future.
Increased Threats
Security intimidations are the significant differences between previous technology and IoT. The threat ratio is greater than the previous technology. The reasons for increased security threats are given below:
Cyber Security Risk = Threat Level + Points of Exposure + Probability of Attack/Cybersecurity Measure Implemented
- Point of Exposure
The number of connected devices, systems, and the applications along with the end-user offer different point of acquaintance.
- New Attack Points
Every new device we connect to the platform might become an attack point. That simply means the chances of attacks are higher.
- Attack Impact
In complex and simple infrastructure, as more devices are connected, the impact of attacks is higher. As these devices are built and connected to different standards and goals. The threat level for hacking a device is also increased accordingly.
- New Threats
As technology is becoming complex for the infrastructure the possibilities for threats also increases. Cybersecurity measure should be professionally implemented.
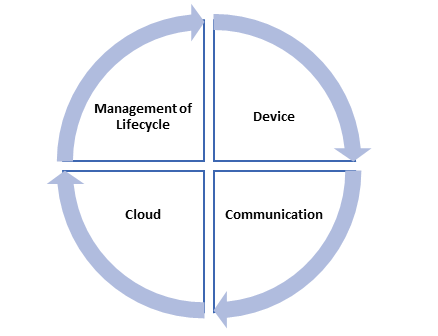
IoT Layers for Security
Internet of things architecture requires different security technique that is multi-layered. These layers and techniques support in seamless working by offering end-to-end security. This security is from any device to the cloud and surrounded among the complete lifecycle of IoT solution. The layers are discussed below:
- Device
This is the 1st layer of security that is related to the hardware or physical devices of the internet of things solutions. It increases the security of hardware as well as software. The major security components of this layer are physical security, device authentication, chip security, and device identity etc.
- Communication
The 2nd layer is the communication that is responsible for the network connectivity. It includes the medium that use to transfer and receive data. Sensitive data is transferred to the physical layer, networking layer and application layer. This transaction of sensitive data is secure and the chances of threats increase. The significant components include firewall, IDS, IPS, end-to-end encryption and access control etc.
- Cloud
Cloud layer of IoT security refers to the backend of software. The data from the devices is analyzed, interpreted and consumed to generate insights and take actions. The cloud IoT service provider is expected to provide efficient and secure services and protected way. The security components are platform integrity verification, integrity verification, and data at rest.
- Management of Lifecycle
The complete IoT lifecycle should be secure with continuous processes. There is a strong need adopt up-to-date solutions. It ensures the security at different levels from the initial installation, device manufacturing until the end of the procedure. The security components of lifecycle management are a risk assessment, auditing, policies, activity tracking, vendor control and user awareness etc.
Automate Security Responsibilities
A wide range of IoT devices are manually handling security responsibilities. But in order to provide today’s IoT solutions this manual handling is not sufficient. Therefore, security automation should be adopted. The implementation of security automation techniques merge the solutions and AI is playing an important role in this regard.
Common IoT Attackers
Today we’re facing a different type of IoT security hackers. Some of the main types of attackers are given below:
Terrorists: These are the professional attackers.
Cyber espionage Syndicates: The organized groups of attackers.
Petty Offenders: Low-level cybersecurity criminals
The cybersecurity attackers are classified according to their capabilities and goals in the form of group or individual. These IoT security attackers may accomplish different results. For instance, an experienced cybercriminal can dodge the IDS signature deduction tool but the new hobbyists couldn’t do that.
The IoT security should be measured and identified by the vendors at a different level. Security indication is becoming the major concern because cybersecurity attackers are required to stop.









 Saudi Arabia (English)
Saudi Arabia (English) United Kingdom
United Kingdom Global Site
Global Site